Overview
Cosign is a command line utility that can sign and verify software artifact, such as container images and blobs.
Installation
https://docs.sigstore.dev/system_config/installation/
wget https://github.com/sigstore/cosign/releases/download/v2.2.3/cosign-darwin-arm64 chmod +x cosign-darwin-arm64 sudo cp cosign-darwin-arm64 /usr/local/bin/cosign
Signing a Blob
> cosign sign-blob <file> --bundle cosign.bundle
Output:
Using payload from: gotk-components.yaml Generating ephemeral keys... Retrieving signed certificate... The sigstore service, hosted by sigstore a Series of LF Projects, LLC, is provided pursuant to the Hosted Project Tools Terms of Use, available at https://lfprojects.org/policies/hosted-project-tools-terms-of-use/. Note that if your submission includes personal data associated with this signed artifact, it will be part of an immutable record. This may include the email address associated with the account with which you authenticate your contractual Agreement. This information will be used for signing this artifact and will be stored in public transparency logs and cannot be removed later, and is subject to the Immutable Record notice at https://lfprojects.org/policies/hosted-project-tools-immutable-records/. By typing 'y', you attest that (1) you are not submitting the personal data of any other person; and (2) you understand and agree to the statement and the Agreement terms at the URLs listed above. Are you sure you would like to continue? [y/N] y Your browser will now be opened to: https://oauth2.sigstore.dev/auth/auth?access_type=online&client_id=sigstore&code_challenge=1cboQoe9SlmimuCDgYZheH1MrByX9epG7ceMPs9uKWg&code_challenge_method=S256&nonce=2ddexWMzBTyUEvDVBOwx9Mb15Zc&redirect_uri=http%3A%2F%2Flocalhost%3A64841%2Fauth%2Fcallback&response_type=code&scope=openid+email&state=2ddexTMg9MYyDZlV9aKb6QkSLWn Successfully verified SCT... using ephemeral certificate: -----BEGIN CERTIFICATE----- ... -----END CERTIFICATE----- tlog entry created with index: 77825201 using ephemeral certificate: -----BEGIN CERTIFICATE----- ... -----END CERTIFICATE----- Wrote bundle to file cosign.bundle MEQCIEI2pfffhoN3xAFLF0ffuACLk00Z4NVr6XlLFUFOlTT+AiAXivuc3Zja7e4hjR3r63NOlZ9pvysWoaB3CADNaCMmAQ==
Verifying
cosign verify-blob gotk-components.yaml --bundle cosign.bundle --certificate-identity=jmehan@yahoo.com --certificate-oidc-issuer=https://github.com/login/oauth
Verified OK
Generating a Key Pair
cosign generate-key-pair
Enter password for private key: Enter password for private key again: Private key written to cosign.key Public key written to cosign.pub
Signing and Verifying a Container
Get the digest of the image
docker inspect --format='{{index .RepoDigests 0}}' ncydacrinprogress.azurecr.io/cybersecuritydome/kafka-azure-sink:22.0.1-3868980
ncydacrinprogress.azurecr.io/cybersecuritydome/kafka-azure-sink@sha256:2fbb556a6a2b68466def031067c18411693c6a9f3b5e4b16c1677e28c0029172
Sign
cosign sign --key cosign.key ncydacrinprogress.azurecr.io/cybersecuritydome/kafka-azure-sink@sha256:2fbb556a6a2b68466def031067c18411693c6a9f3b5e4b16c1677e28c0029172
Enter password for private key: WARNING: "ncydacrinprogress.azurecr.io/cybersecuritydome/kafka-azure-sink" appears to be a private repository, please confirm uploading to the transparency log at "https://rekor.sigstore.dev" Are you sure you would like to continue? [y/N] y The sigstore service, hosted by sigstore a Series of LF Projects, LLC, is provided pursuant to the Hosted Project Tools Terms of Use, available at https://lfprojects.org/policies/hosted-project-tools-terms-of-use/. Note that if your submission includes personal data associated with this signed artifact, it will be part of an immutable record. This may include the email address associated with the account with which you authenticate your contractual Agreement. This information will be used for signing this artifact and will be stored in public transparency logs and cannot be removed later, and is subject to the Immutable Record notice at https://lfprojects.org/policies/hosted-project-tools-immutable-records/. By typing 'y', you attest that (1) you are not submitting the personal data of any other person; and (2) you understand and agree to the statement and the Agreement terms at the URLs listed above. Are you sure you would like to continue? [y/N] y tlog entry created with index: 77828277 Pushing signature to: ncydacrinprogress.azurecr.io/cybersecuritydome/kafka-azure-sink
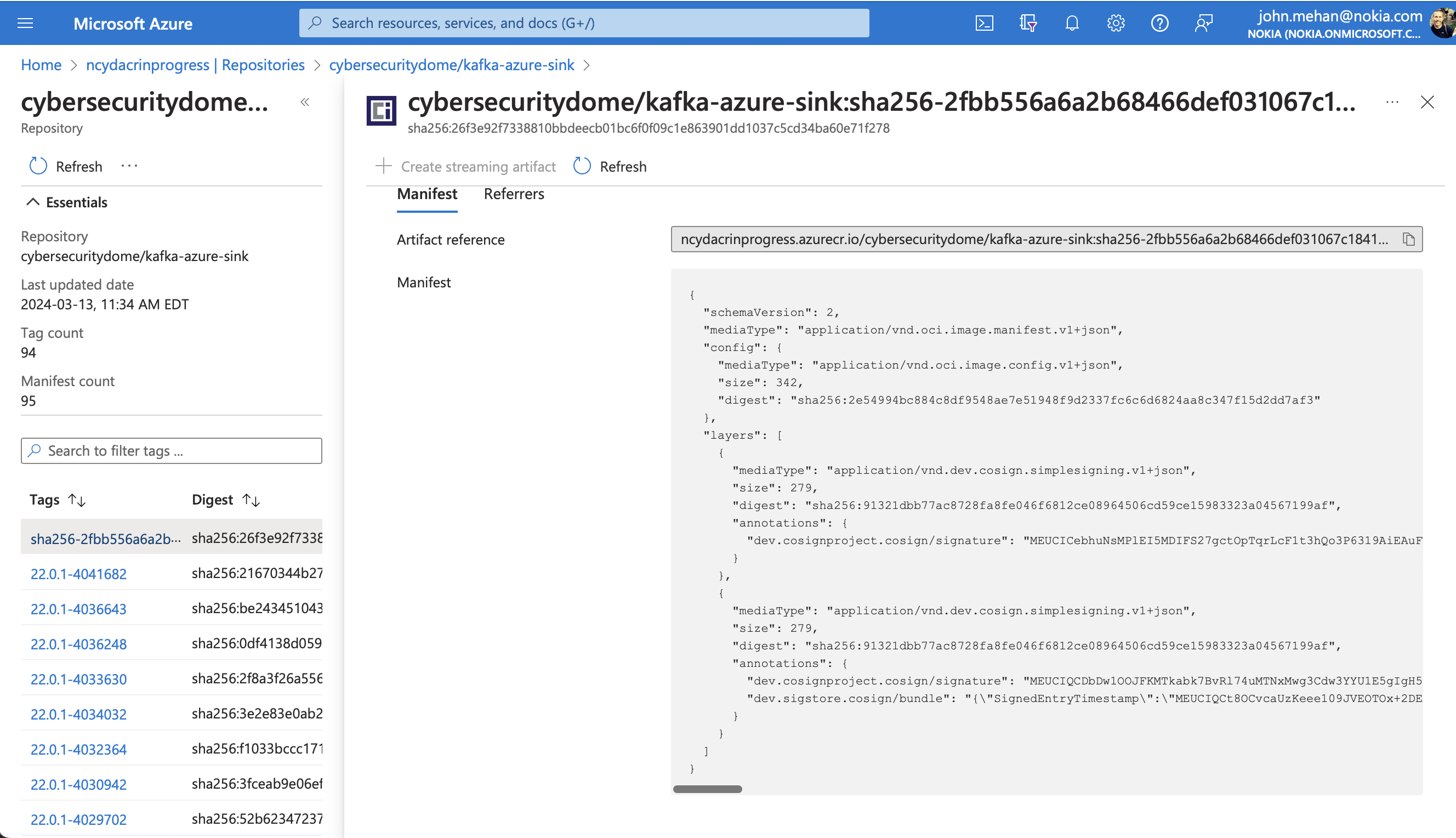
View Container in Azure
Verify Signature
cosign verify --key cosign.pub ncydacrinprogress.azurecr.io/cybersecuritydome/kafka-azure-sink@sha256:2fbb556a6a2b68466def031067c18411693c6a9f3b5e4b16c1677e28c0029172
Verification for ncydacrinprogress.azurecr.io/cybersecuritydome/kafka-azure-sink@sha256:2fbb556a6a2b68466def031067c18411693c6a9f3b5e4b16c1677e28c0029172 -- The following checks were performed on each of these signatures: - The cosign claims were validated - Existence of the claims in the transparency log was verified offline - The signatures were verified against the specified public key
[
{
"critical": {
"identity": {
"docker-reference": "ncydacrinprogress.azurecr.io/cybersecuritydome/kafka-azure-sink"
},
"image": {
"docker-manifest-digest": "sha256:2fbb556a6a2b68466def031067c18411693c6a9f3b5e4b16c1677e28c0029172"
},
"type": "cosign container image signature"
},
"optional": {
"Bundle": {
"SignedEntryTimestamp": "MEUCIQCt8OCvcaUzKeee109JVEOTOx+2DEKA5SCEd5R/BaXA1QIgI91Ebfv6MEx5F2OW05yU8kSxS3kwrXAP5/beU7CQBc0=",
"Payload": {
"body": "eyJhcGlWZXJzaW9uIjoiMC4wLjEiLCJraW5kIjoiaGFzaGVkcmVrb3JkIiwic3BlYyI6eyJkYXRhIjp7Imhhc2giOnsiYWxnb3JpdGhtIjoic2hhMjU2IiwidmFsdWUiOiI5MTMyMWRiYjc3YWM4NzI4ZmE4ZmUwNDZmNjgxMmNlMDg5NjQ1MDZjZDU5Y2UxNTk4MzMyM2EwNDU2NzE5OWFmIn19LCJzaWduYXR1cmUiOnsiY29udGVudCI6Ik1FVUNJUUNEYkR3MU9PSkZLTVRrYWJrN0J2Umw3NHVNVE54TXdnM0NkdzNZWVUxRTVnSWdINWp1UmJRd2tnSnozZEZJNkEreFIxc2tnV2N3NmFsTUdublFKaU9PNC80PSIsInB1YmxpY0tleSI6eyJjb250ZW50IjoiTFMwdExTMUNSVWRKVGlCUVZVSk1TVU1nUzBWWkxTMHRMUzBLVFVacmQwVjNXVWhMYjFwSmVtb3dRMEZSV1VsTGIxcEplbW93UkVGUlkwUlJaMEZGTmpnNE56a3pPVlZtVkRsUFVFMUlkbE5VTjA5Q1psUXhlRUYyWVFwcFVsQmlRakZJZVdGeUsyNUdRMVZYVm5aWU4wVjJhVVZRVEhoVVdsSk9VVEpCTkU5UVMwRnJSRzh4WlROSVNUaFBSbFJ5T1ZwQlNYbFJQVDBLTFMwdExTMUZUa1FnVUZWQ1RFbERJRXRGV1MwdExTMHRDZz09In19fX0=",
"integratedTime": 1710344087,
"logIndex": 77828277,
"logID": "c0d23d6ad406973f9559f3ba2d1ca01f84147d8ffc5b8445c224f98b9591801d"
}
}
}
}
]
References
| Reference | URL |
|---|---|
| Cosign Quickstart | https://docs.sigstore.dev/signing/quickstart/ |