...
This sensor does not use a simple checksum or even a more advanced CRC. Instead data integrity is verified by a hash code, generated by multiplying the message bits with the byte sequence generated by a linear feedback shift register (LFSR). This algorithm has been referred to as "an LFSR-based Toeplitz hash" in some of the literature.
Hash Algorithm
1. Generate LSFR sequence equal to the length of the message.
In our case, our message is 32 bits long, so we will need 32 values.
...
| Start Value | Shift Right | XOR with 0x18 if MSB =1 (flip bits 3 and 4) | Xor | Value | |
|---|---|---|---|---|---|
| 1 | 0111 1100 (0x7C) | → 0011 1110 | NO | - | 0011 1110 (0x3e) |
| 2 | 0011 1110 (0x3e) | → 0001 1111 | NO | - | 0001 1111 (0x1f) |
| 3 | 0001 1111 (0x1f) | → 1000 1111 | YES | xor 0x18 | 1001 0111 (0x97) |
| 4 | 1001 0111 (0x97) | → 1100 1011 | YES | xor 0x18 | 1101 0011 (0xd3) |
| 5 | 1101 0011 (0xd3) | → 1110 1001 | YES | xor 0x18 | 1111 0001 (0xf1) |
| ... | |||||
| 32 | 1000 0110 (0x86) | → 0100 0011 | NO | - | 0100 0011 (0x43) |
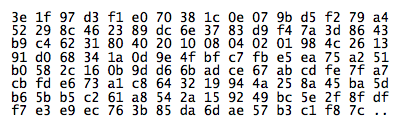
Values
2. Combines the LSFR sequence with message bits to form the final hash value
To compute the message hash value, sequence through the 24 message bits in the order they were received. Since everything here is big-endian, that means proceeding from MSB to LSB. Start by initializing the hash register to the value 0x00. As the message bits are read, for every bit in the message that is a one, exclusive-or the corresponding value (+5) from the LSFR sequence into the hash register.
For example, if the 10th bit is a one, then take the 15th value from the LFSR sequence and exclusive-or it into the hash register. If the message were all zeros, then nothing would be added to the hash register and the result would be the initial value of 0x00.
...