Gradle Dependency Check
The following build.gradle will perform the vulnerability check against our Go project.
build.gradle
apply plugin: 'org.owasp.dependencycheck'
buildscript {
repositories {
mavenCentral()
}
ext {
owaspPluginVersion = '7.0.3'
}
dependencies {
classpath "org.owasp:dependency-check-gradle:${owaspPluginVersion}"
}
}
dependencyCheck {
failOnError = false
format = 'ALL'
outputDirectory = "${buildDir}/reports/owasp"
suppressionFile = "${projectDir}/owasp-suppressions.xml"
analyzers {
experimentalEnabled = true
golangModEnabled = true
pathToGo = '/usr/local/go/bin/go'
}
}
task build() {
// empty
}
build.dependsOn (dependencyCheckAnalyze)
Addressing Vulnerabilities
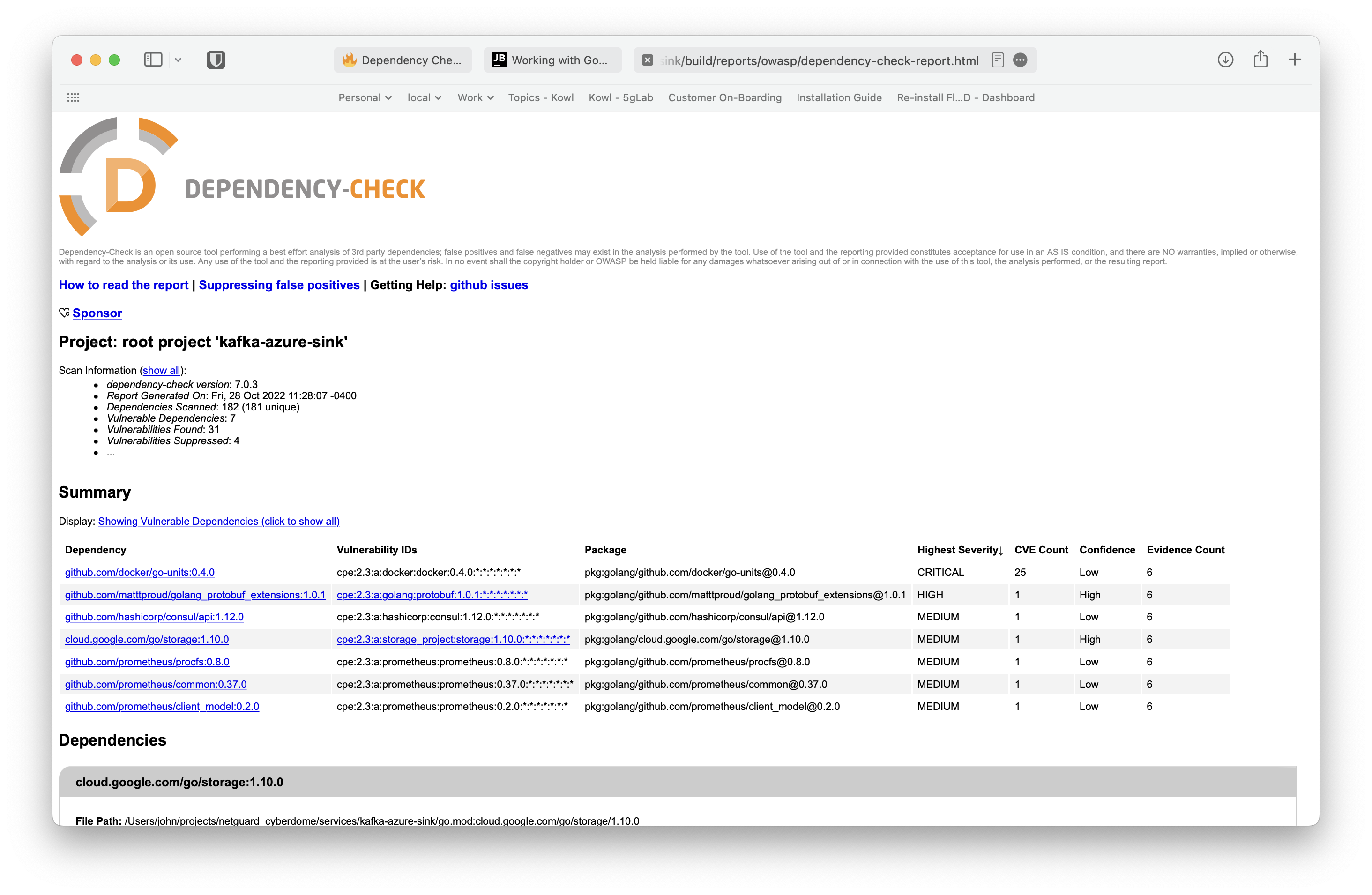
Sample Vulnerability Report
> Task :dependencyCheckAnalyze Verifying dependencies for project kafka-azure-sink Checking for updates and analyzing dependencies for vulnerabilities Generating report for project kafka-azure-sink Found 31 vulnerabilities in project kafka-azure-sink One or more dependencies were identified with known vulnerabilities in kafka-azure-sink: go.mod (pkg:golang/cloud.google.com/go/storage@1.10.0, cpe:2.3:a:storage_project:storage:1.10.0:*:*:*:*:*:*:*) : CVE-2021-20291 go-units@v0.4.0 (pkg:golang/github.com/docker/go-units@0.4.0, cpe:2.3:a:docker:docker:0.4.0:*:*:*:*:*:*:*) : CVE-2014-0047, CVE-2014-0048, CVE-2014-5277, CVE-2014-5278, CVE-2014-5282, CVE-2014-6407, CVE-2014-8178, CVE-2014-8179, CVE-2014-9356, CVE-2014-9358, CVE-2015-3627, CVE-2015-3630, CVE-2015-3631, CVE-2016-3697, CVE-2017-14992, CVE-2019-13139, CVE-2019-13509, CVE-2019-15752, CVE-2019-16884, CVE-2019-5736, CVE-2020-27534, CVE-2021-21284, CVE-2021-21285, CVE-2021-3162, CVE-2022-25365 go.mod (pkg:golang/github.com/hashicorp/consul/api@1.12.0, cpe:2.3:a:hashicorp:consul:1.12.0:*:*:*:*:*:*:*) : CVE-2022-40716 golang_protobuf_extensions@v1.0.1 (pkg:golang/github.com/matttproud/golang_protobuf_extensions@1.0.1, cpe:2.3:a:golang:protobuf:1.0.1:*:*:*:*:*:*:*) : CVE-2021-3121 client_model@v0.2.0 (pkg:golang/github.com/prometheus/client_model@0.2.0, cpe:2.3:a:prometheus:prometheus:0.2.0:*:*:*:*:*:*:*) : CVE-2019-3826 go.mod (pkg:golang/github.com/prometheus/common@0.37.0, cpe:2.3:a:prometheus:prometheus:0.37.0:*:*:*:*:*:*:*) : CVE-2019-3826 go.mod (pkg:golang/github.com/prometheus/procfs@0.8.0, cpe:2.3:a:prometheus:prometheus:0.8.0:*:*:*:*:*:*:*) : CVE-2019-3826 See the dependency-check report for more details.
Dependency Check Report
open build/reports/owasp/dependency-check-report.html
When a vulnerability is found we will need to do the following things:
Update the library
module kafka-azure-sink go 1.18 require ( ... github.com/docker/go-units v0.5.0 )
Issue the following commands:
go mod vendor go mod tidy
Build the project to verify all is well
go build -o ./kafka-azure-sink ./src/cmd/svc
Re-run the Gradle Build
./gradlew build
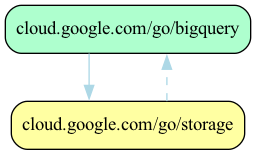
Using GOMOD to Visualize Dependencies
Install gomod - https://github.com/Helcaraxan/gomod
go install github.com/Helcaraxan/gomod@latest
Install graphwiz - https://www.graphviz.org/download/
On Mac:
echo 'eval "$(/opt/homebrew/bin/brew shellenv)"' >> ~/.zprofile brew install graphviz
Usage
gomod graph | dot -Tpng -o out.png open out.png
Example using filter and including tests:
gomod graph 'rdeps(cloud.google.com/go/storage:test)' | dot -Tpng -o out.png open out.jpg
Can't Find the Dependency?
go mod graph |grep <dependency>