...
You will need to first search for Sentinel and then create a workspace. Then you can add a sentinel instance to your workspace.
...
Data Collection
Azure Sentinel has a number of connectors that can be used to send data and logs to Azure.
Connectors
Kubernetes Connector
We can use fluent-bit's build in azure connector to send data to Azure. See Fluentbit to Azure Analytics.
...
| Code Block |
|---|
$ sudo /opt/microsoft/omsagent/bin/uninstall # Purge - might be the better way to uninstall $ wget -O onboard_agent.sh https://raw.githubusercontent.com/Microsoft/OMS-Agent-for-Linux/master/installer/scripts/onboard_agent.sh && sudo sh onboard_agent.sh --purge |
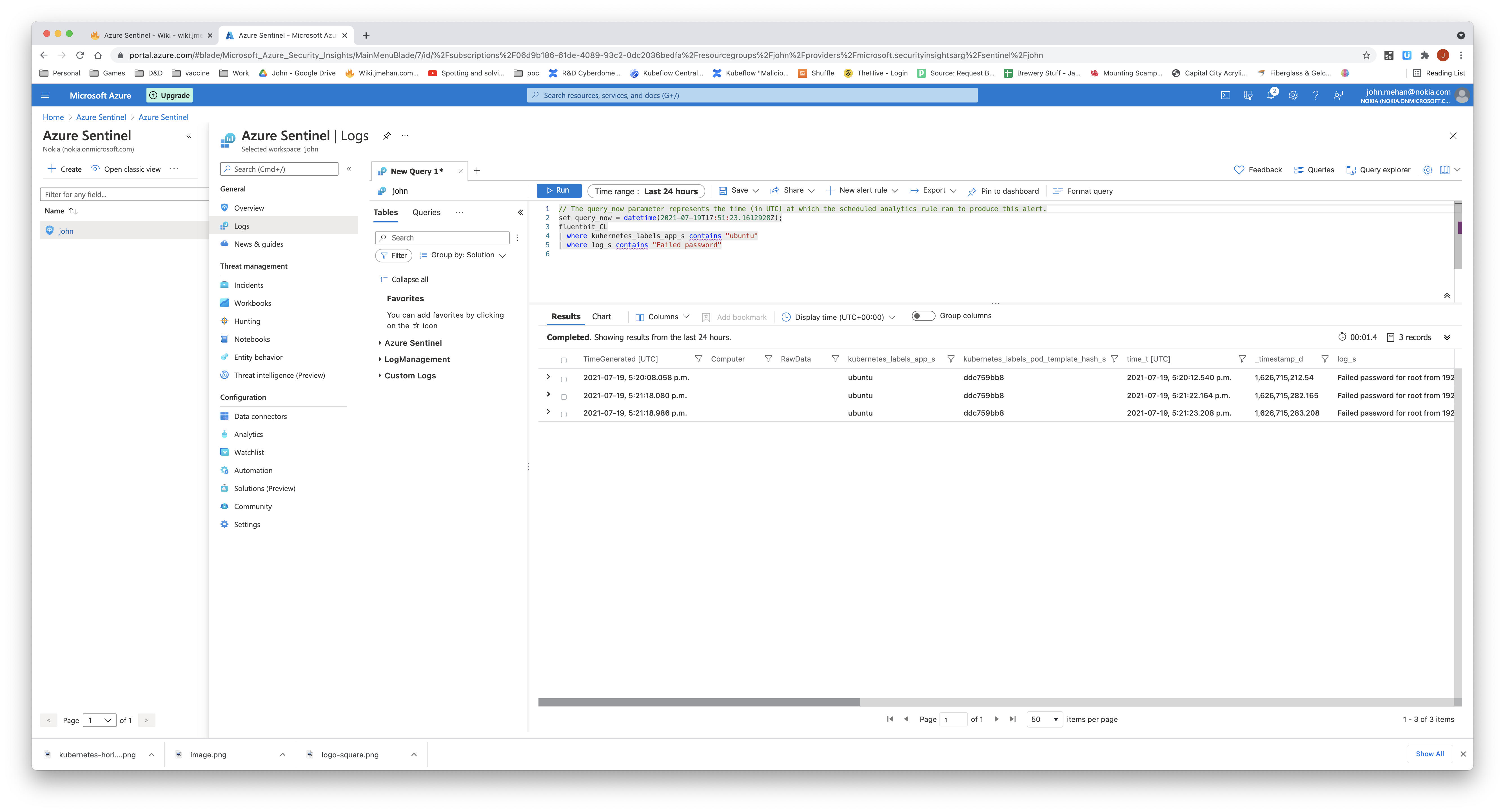
Querying the Logs
From the Log screen, we can create queries to search our logs.
Query Examples
| Code Block |
|---|
Syslog
| where Facility in ("authpriv","auth")
| extend c = extract( "Accepted\\s(publickey|password|keyboard-interactive/pam)\\sfor ([^\\s]+)",1,SyslogMessage)
| where isnotempty(c)
| count
Syslog
| where Facility in ("authpriv","auth")
| where SyslogMessage contains "authentication failure "
| count
// Search in multiple tables
// Search both Syslog and Event tables for the term "login".
search in (Syslog, Event) "authentication failure"
| where TimeGenerated > ago(24h) // return records from the last 24 hours
// All Syslog with errors
// Last 100 Syslog with erros.
Syslog
| where SeverityLevel == "err" or SeverityLevel == "error"
| top 100 by TimeGenerated desc
//login errors
Syslog
| where SeverityLevel == "err" or SeverityLevel == "error"
| where Facility == "auth"
| where SyslogMessage contains "kex_exchange_identification"
//any auth errors
Syslog
| where SeverityLevel == "err" or SeverityLevel == "error"
| where Facility == "auth"
| count
//failed login
Syslog
| where Facility == "auth"
| where SyslogMessage contains "Failed password"
| order by EventTime asc
| count
//failed login with extraction of fields
Syslog
| where Facility == "auth"
| where SyslogMessage contains "Failed password"
| extend user = extract("Failed password for invalid user (.*) from (.*) port (.*) (.*)", 1, SyslogMessage, typeof(string))
| extend remoteIp = extract("Failed password for invalid user (.*) from (.*) port (.*) (.*)", 2, SyslogMessage, typeof(string))
| extend port = extract("Failed password for invalid user (.*) from (.*) port (.*) (.*)", 3, SyslogMessage, typeof(string))
| extend protocol = extract("Failed password for invalid user (.*) from (.*) port (.*) (.*)", 4, SyslogMessage, typeof(string))
| order by EventTime asc
//kubernetes logs gathered using fluent-bit
fluentbit_CL
| where kubernetes_labels_app_s contains "ubuntu"
| where log_s contains "Failed password"
|
...