Create an Azure Sentinel Instance
https://azure.microsoft.com/en-ca/services/azure-sentinel/
https://portal.azure.com/#home
You will need to first search for Sentinel and then create a workspace. Then you can add a sentinel instance to your workspace.
Data Collection
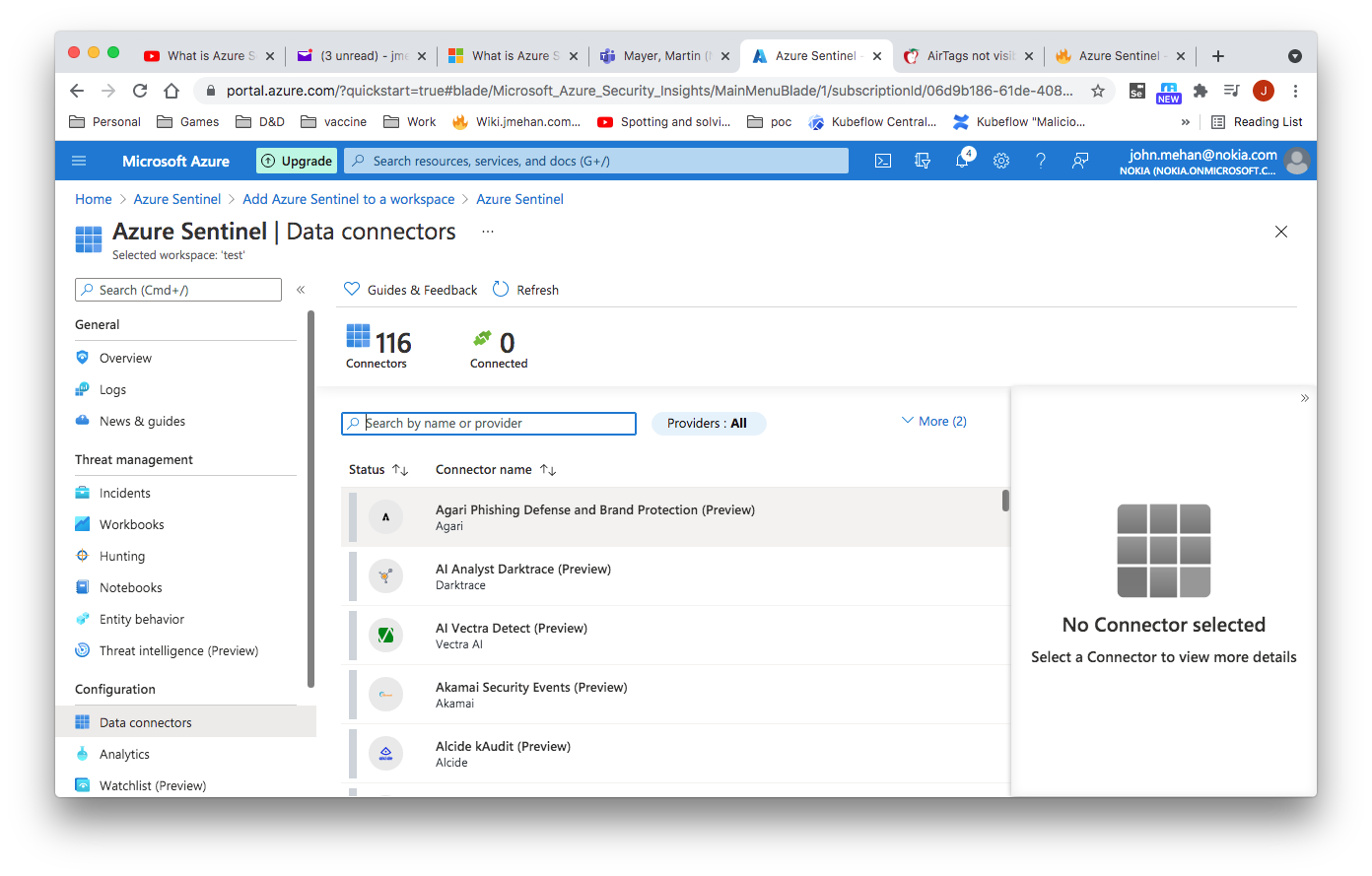
Azure Sentinel has a number of connectors that can be used to send data and logs to Azure.
Kubernetes Connector
We can use fluent-bit's build in azure connector to send data to Azure. See Fluentbit to Azure Analytics.
Common Event Format
Common Event Format (CEF) is an industry standard format on top of Syslog messages, used by many security vendors to allow event interoperability among different platforms. By connecting your CEF logs to Azure Sentinel, you can take advantage of search & correlation, alerting, and threat intelligence enrichment for each log.
Syslog Connector
https://docs.microsoft.com/en-us/azure/sentinel/connect-syslog
Install the Linux agent
wget https://raw.githubusercontent.com/Microsoft/OMS-Agent-for-Linux/master/installer/scripts/onboard_agent.sh && sh onboard_agent.sh -w xxx -s xxx -d opinsights.azure.com
Output
Uninstall
$ sudo /opt/microsoft/omsagent/bin/uninstall # Purge - might be the better way to uninstall $ wget -O onboard_agent.sh https://raw.githubusercontent.com/Microsoft/OMS-Agent-for-Linux/master/installer/scripts/onboard_agent.sh && sudo sh onboard_agent.sh --purge
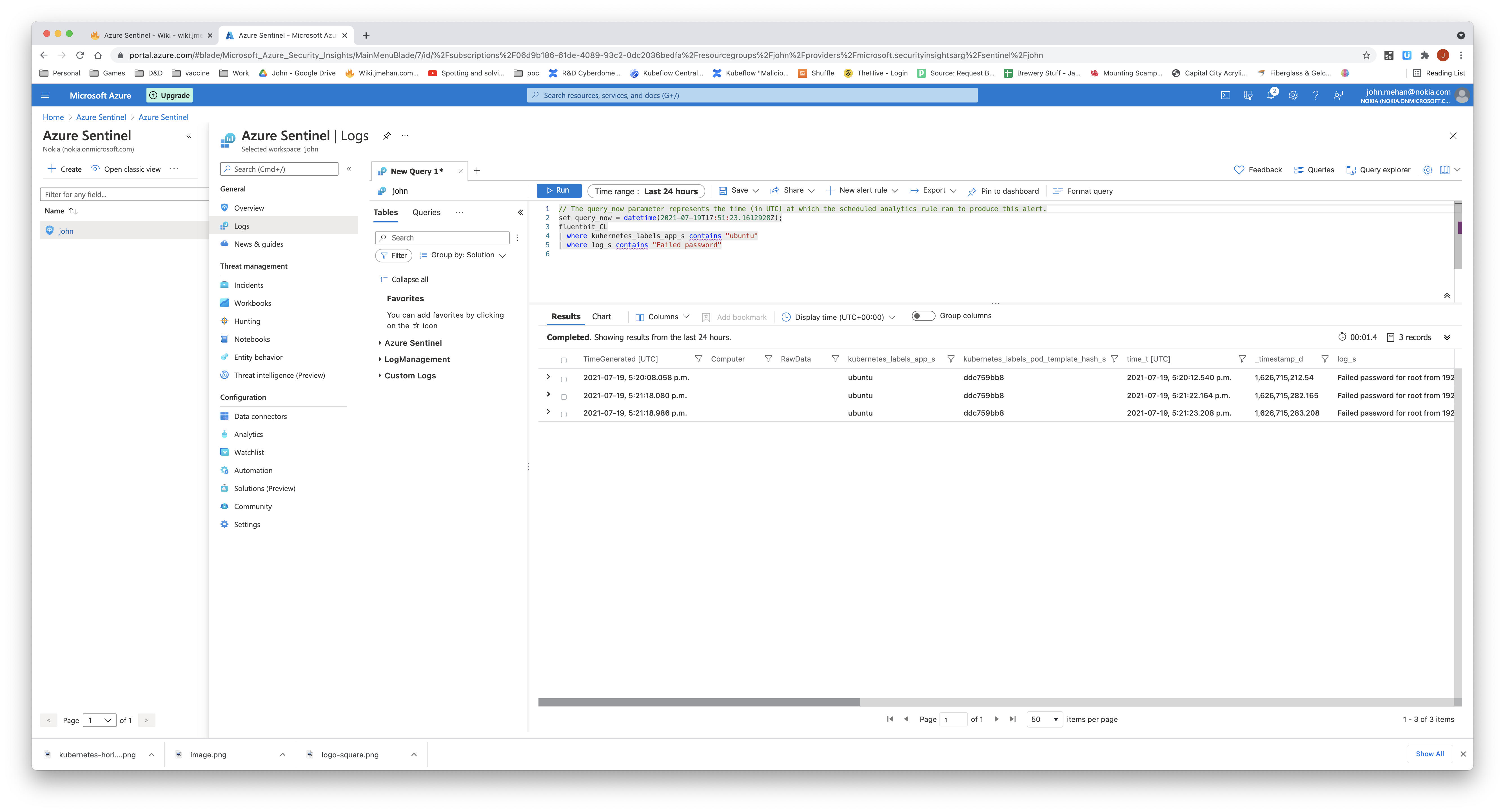
Querying the Logs
From the Log screen, we can create queries to search our logs.
Query Examples
Syslog
| where Facility in ("authpriv","auth")
| extend c = extract( "Accepted\\s(publickey|password|keyboard-interactive/pam)\\sfor ([^\\s]+)",1,SyslogMessage)
| where isnotempty(c)
Syslog
| where Facility in ("authpriv","auth")
| where SyslogMessage contains "authentication failure "
// Search in multiple tables
// Search both Syslog and Event tables for the term "login".
search in (Syslog, Event) "authentication failure"
| where TimeGenerated > ago(24h) // return records from the last 24 hours
// All Syslog with errors
// Last 100 Syslog with erros.
Syslog
| where SeverityLevel == "err" or SeverityLevel == "error"
| top 100 by TimeGenerated desc
//login errors
Syslog
| where SeverityLevel == "err" or SeverityLevel == "error"
| where Facility == "auth"
| where SyslogMessage contains "kex_exchange_identification"
//any auth errors
Syslog
| where SeverityLevel == "err" or SeverityLevel == "error"
| where Facility == "auth"
//failed login
Syslog
| where Facility == "auth"
| where SyslogMessage contains "Failed password"
| order by EventTime asc
//failed login with extraction of fields
Syslog
| where Facility == "auth"
| where SyslogMessage contains "Failed password"
| extend user = extract("Failed password for invalid user (.*) from (.*) port (.*) (.*)", 1, SyslogMessage, typeof(string))
| extend remoteIp = extract("Failed password for invalid user (.*) from (.*) port (.*) (.*)", 2, SyslogMessage, typeof(string))
| extend port = extract("Failed password for invalid user (.*) from (.*) port (.*) (.*)", 3, SyslogMessage, typeof(string))
| extend protocol = extract("Failed password for invalid user (.*) from (.*) port (.*) (.*)", 4, SyslogMessage, typeof(string))
| order by EventTime asc
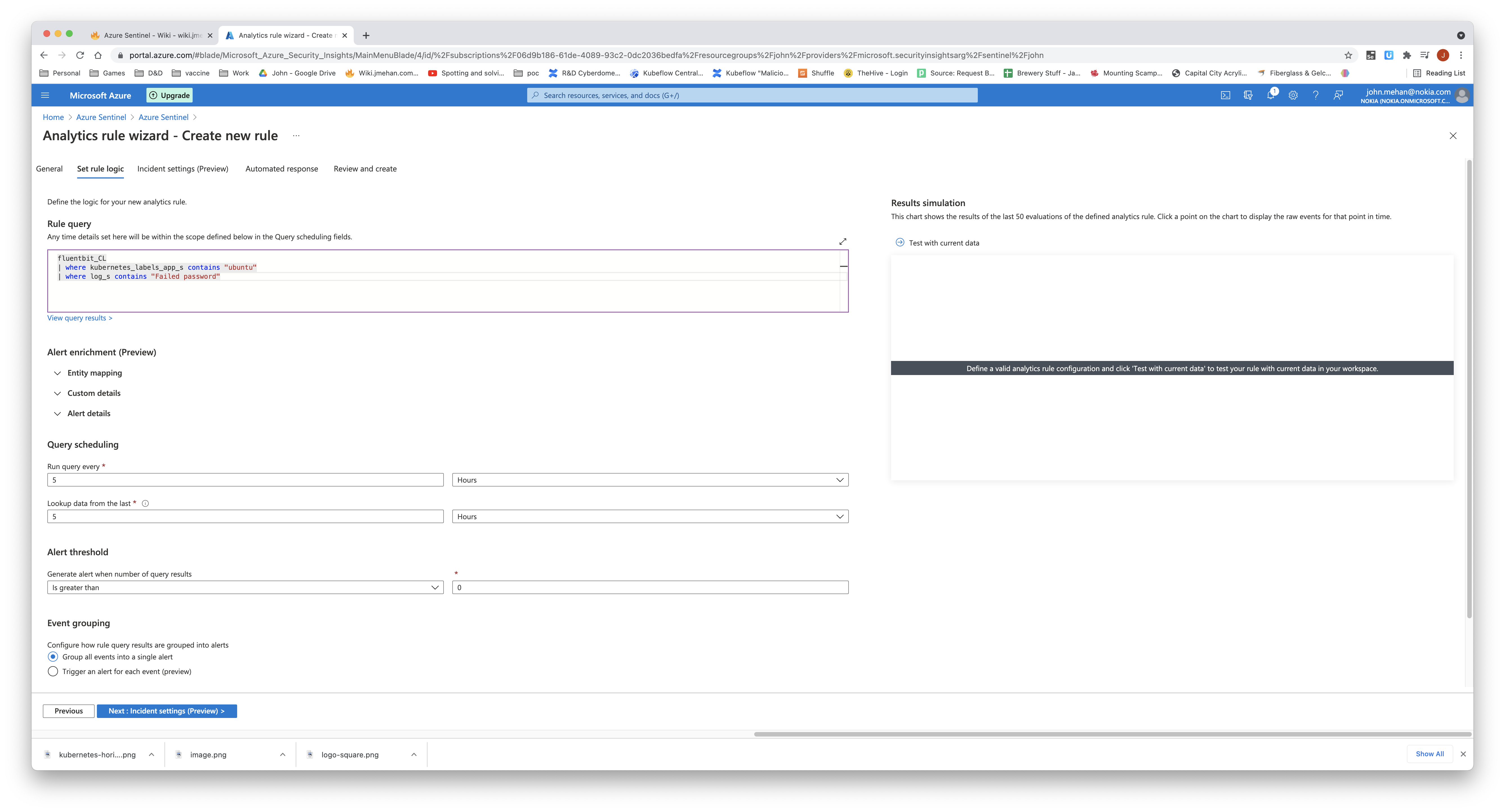
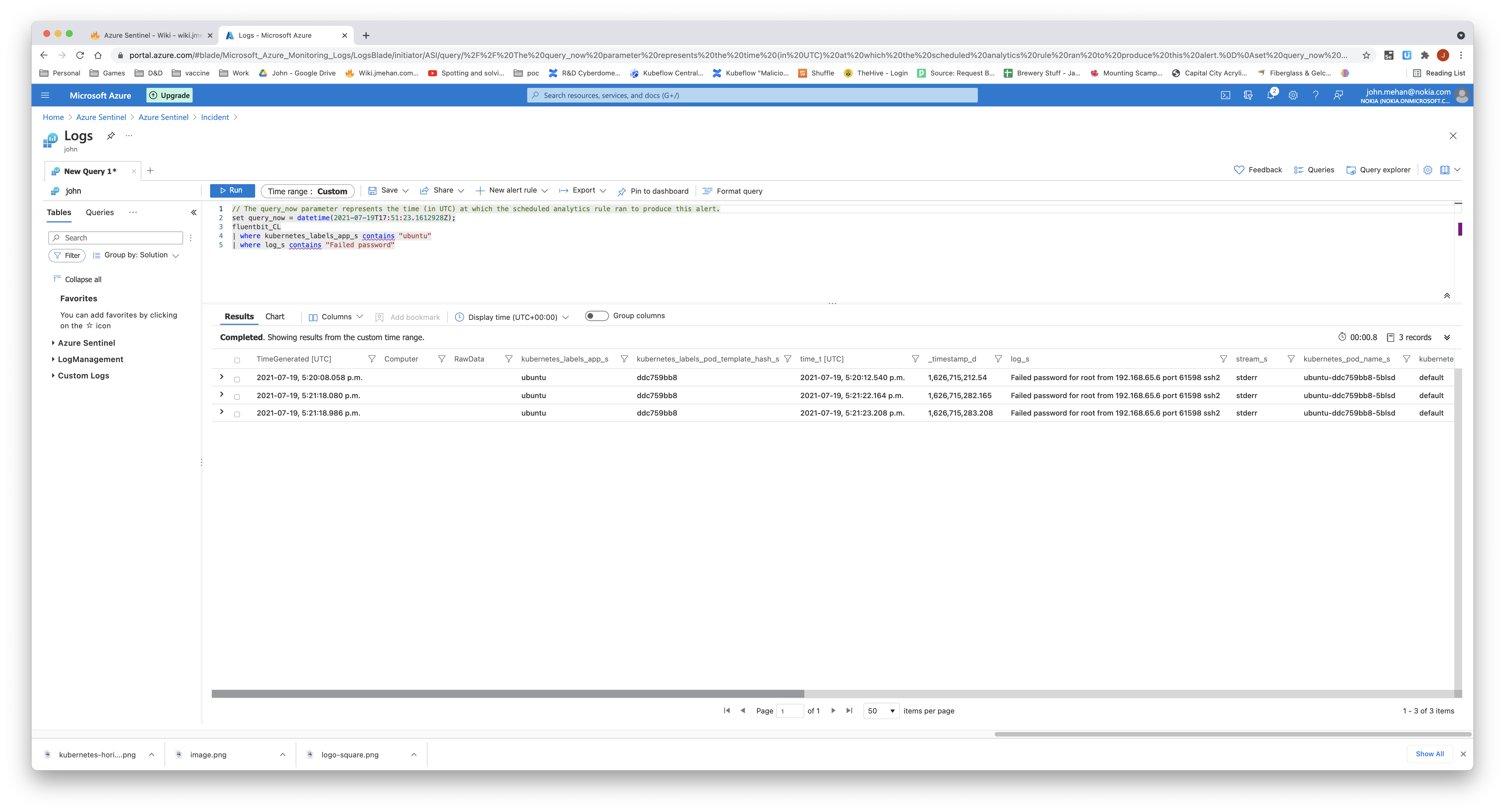
//kubernetes logs gathered using fluent-bit
fluentbit_CL
| where kubernetes_labels_app_s contains "ubuntu"
| where log_s contains "Failed password"
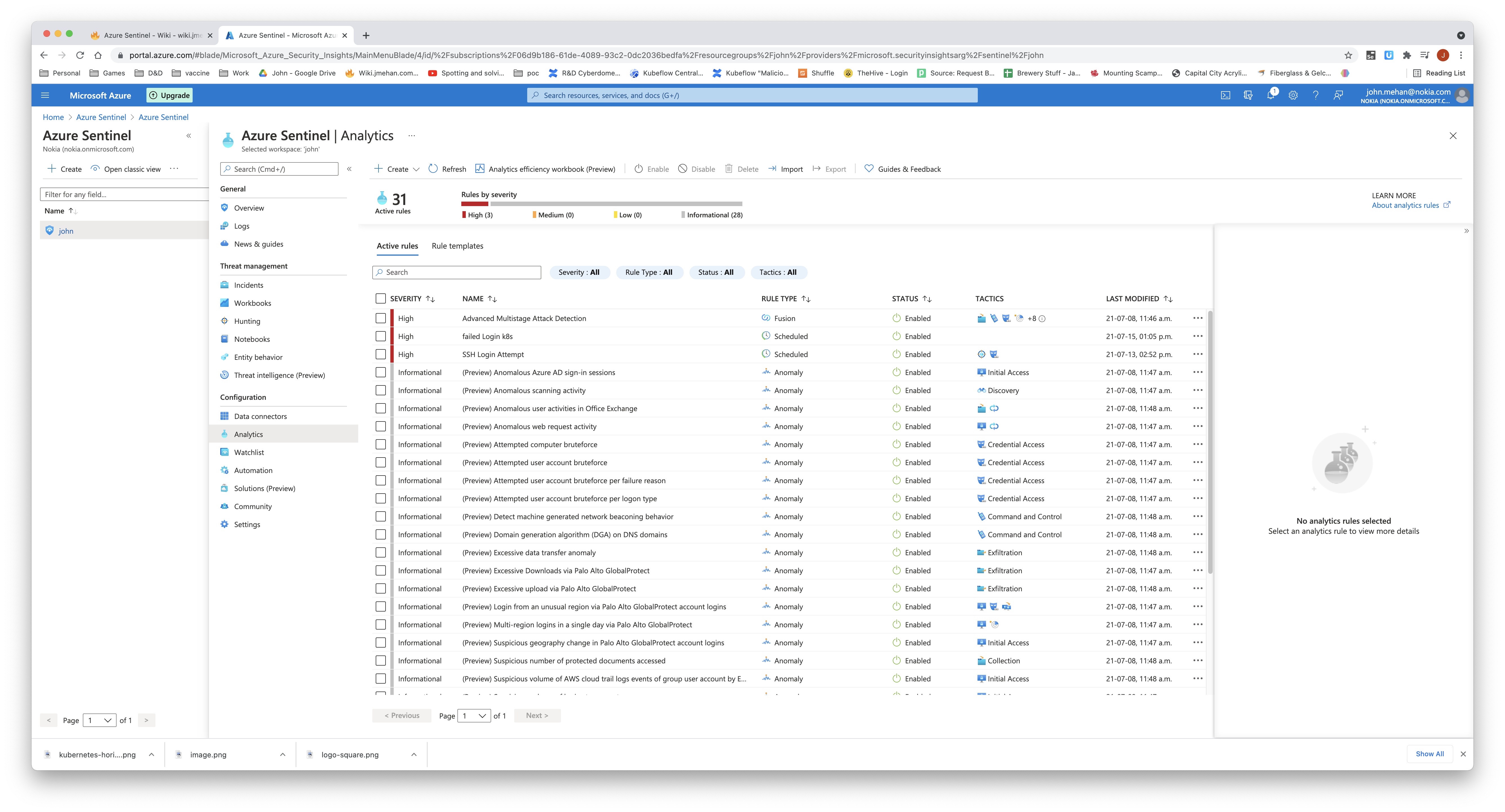
Analytics
Navigate to the Analytics page by clicking Analytics in the left side menu.
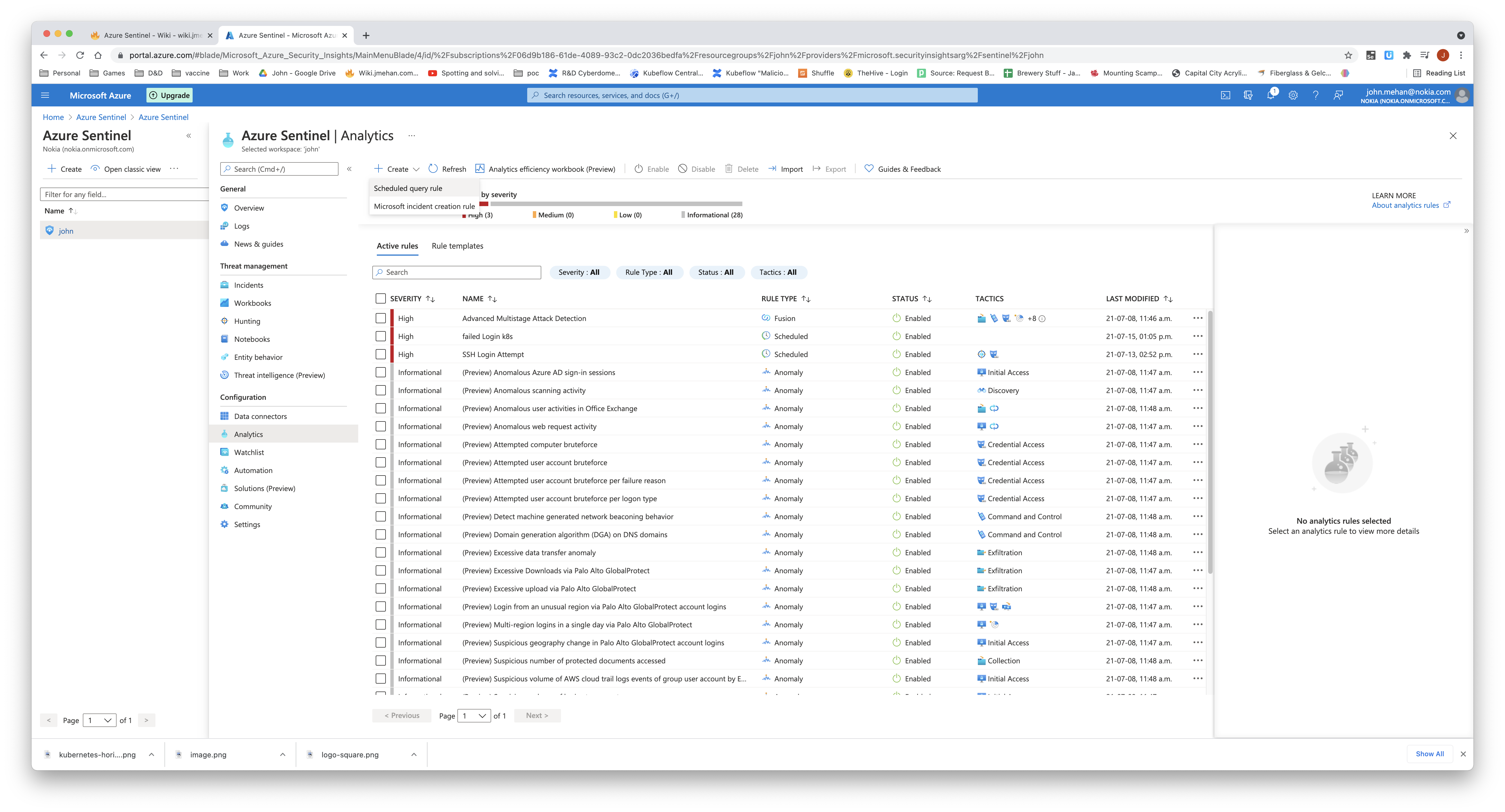
Create a Rule
To create a new rule, simply click the Create pull down and select Scheduled Query Rule.
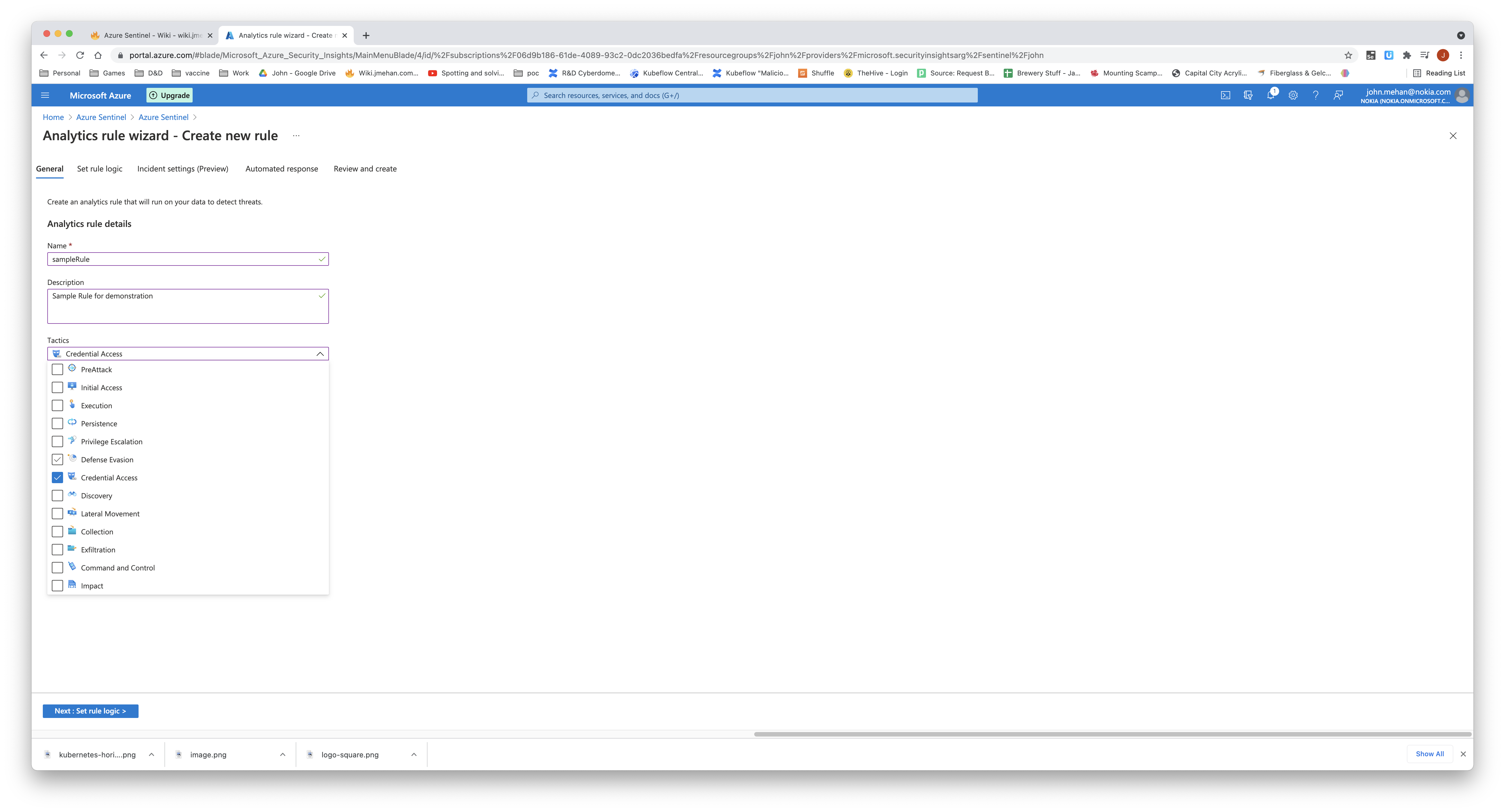
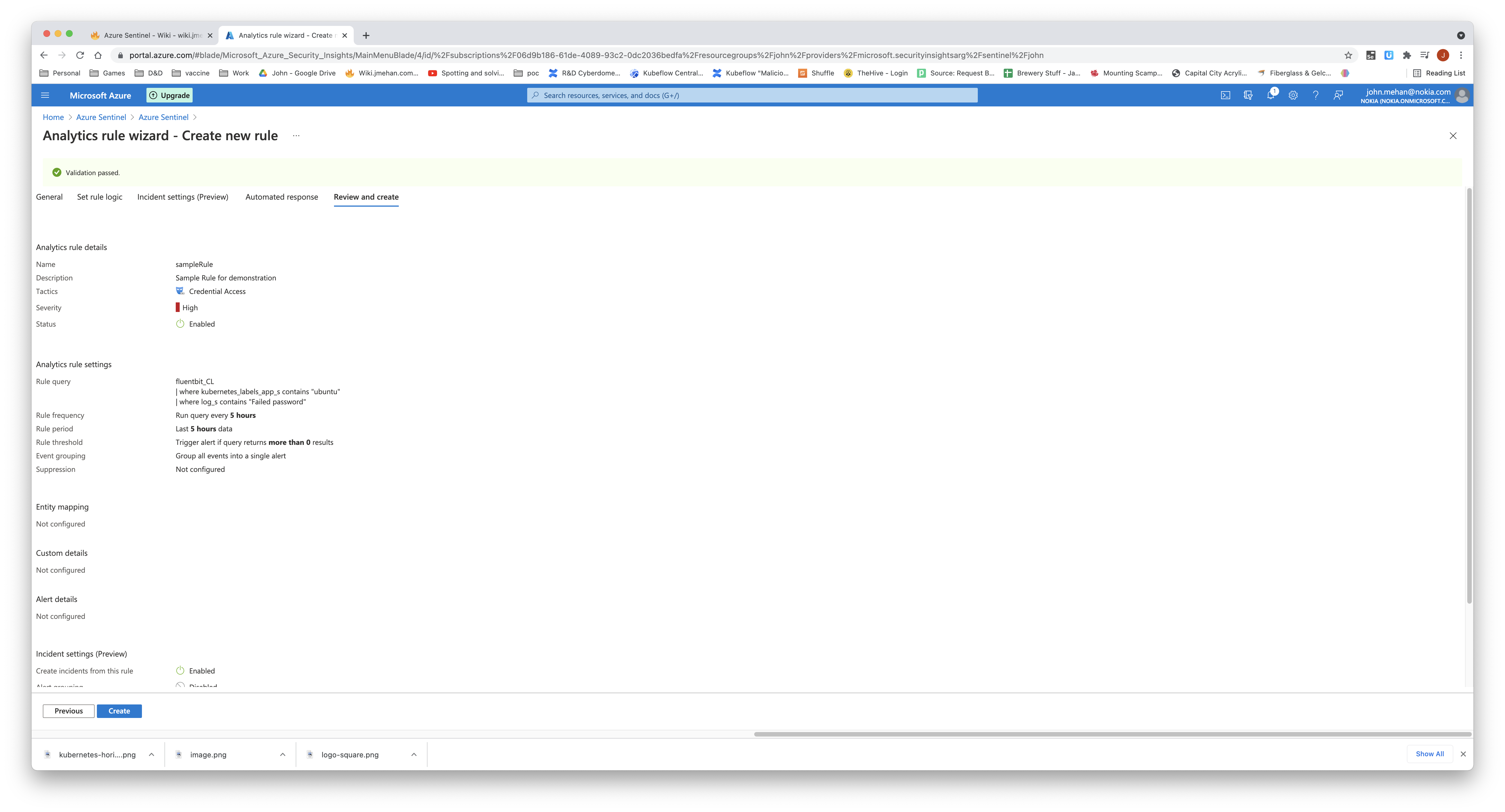
Define the general information about the rule: name, description. You also have the ability to categorize the rule into group of tactics.
Define the query, how often to run the query and the alert threshold.
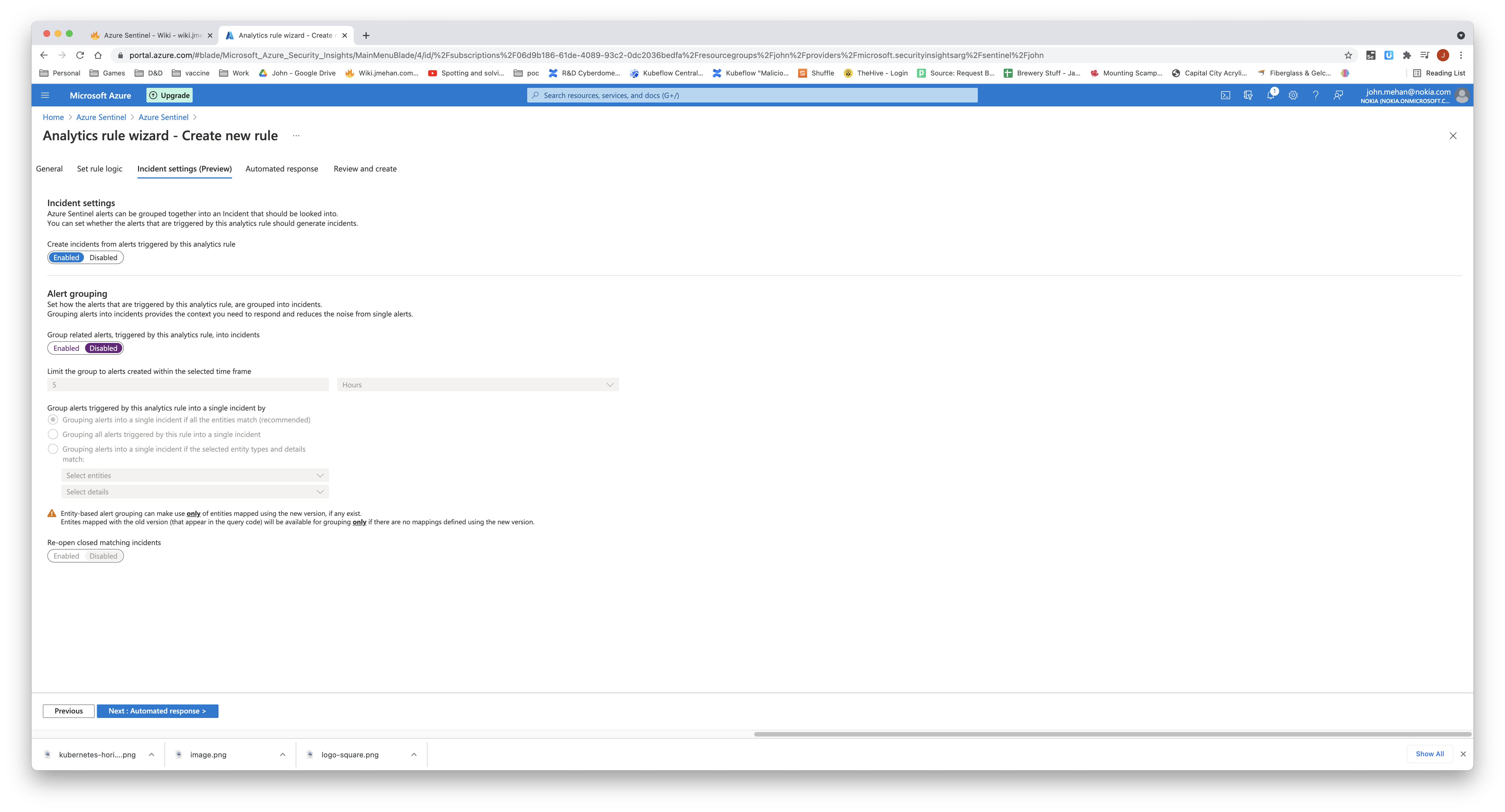
Enable incident creation
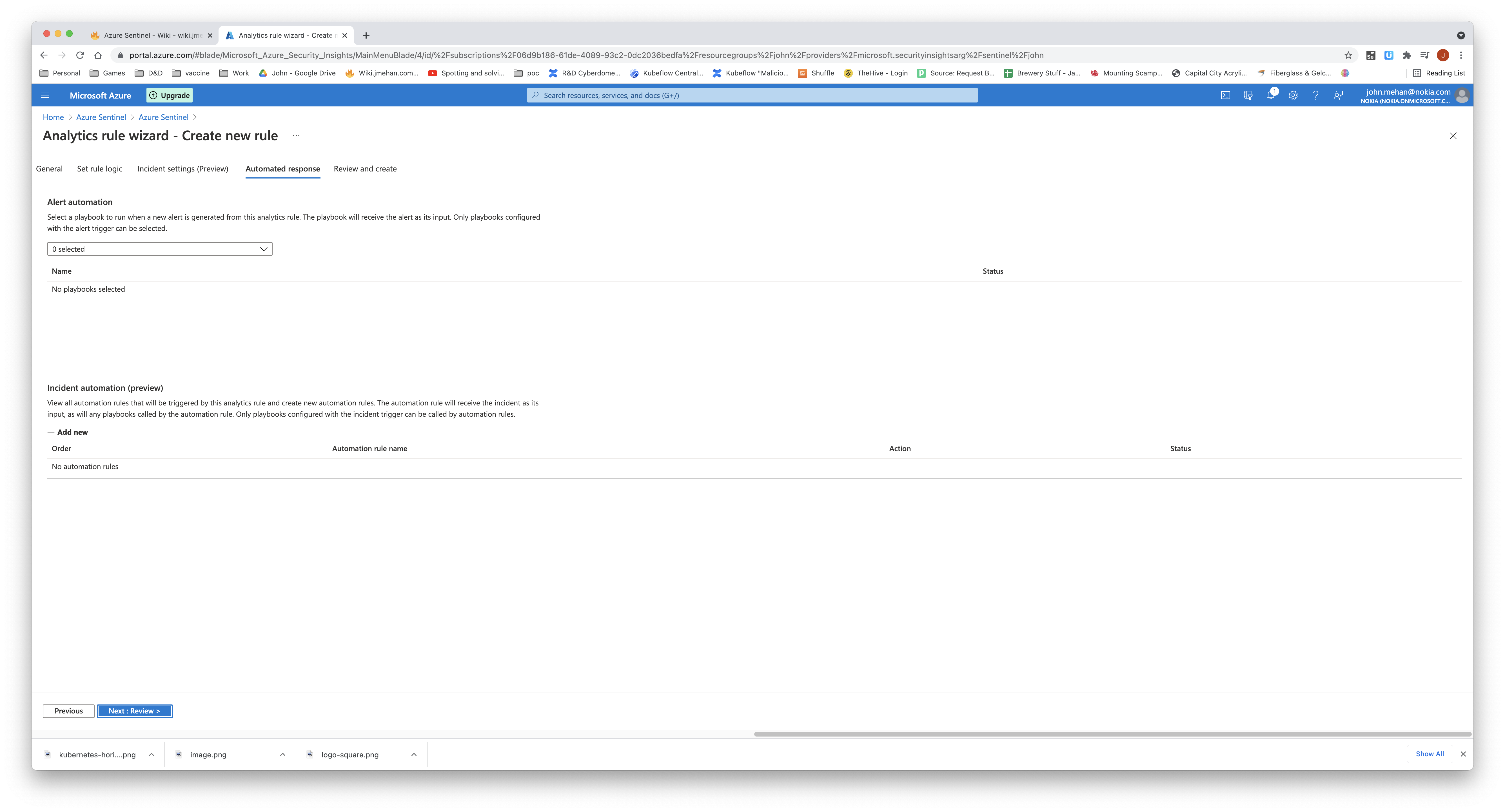
Define Response
Review and Save
Incidents
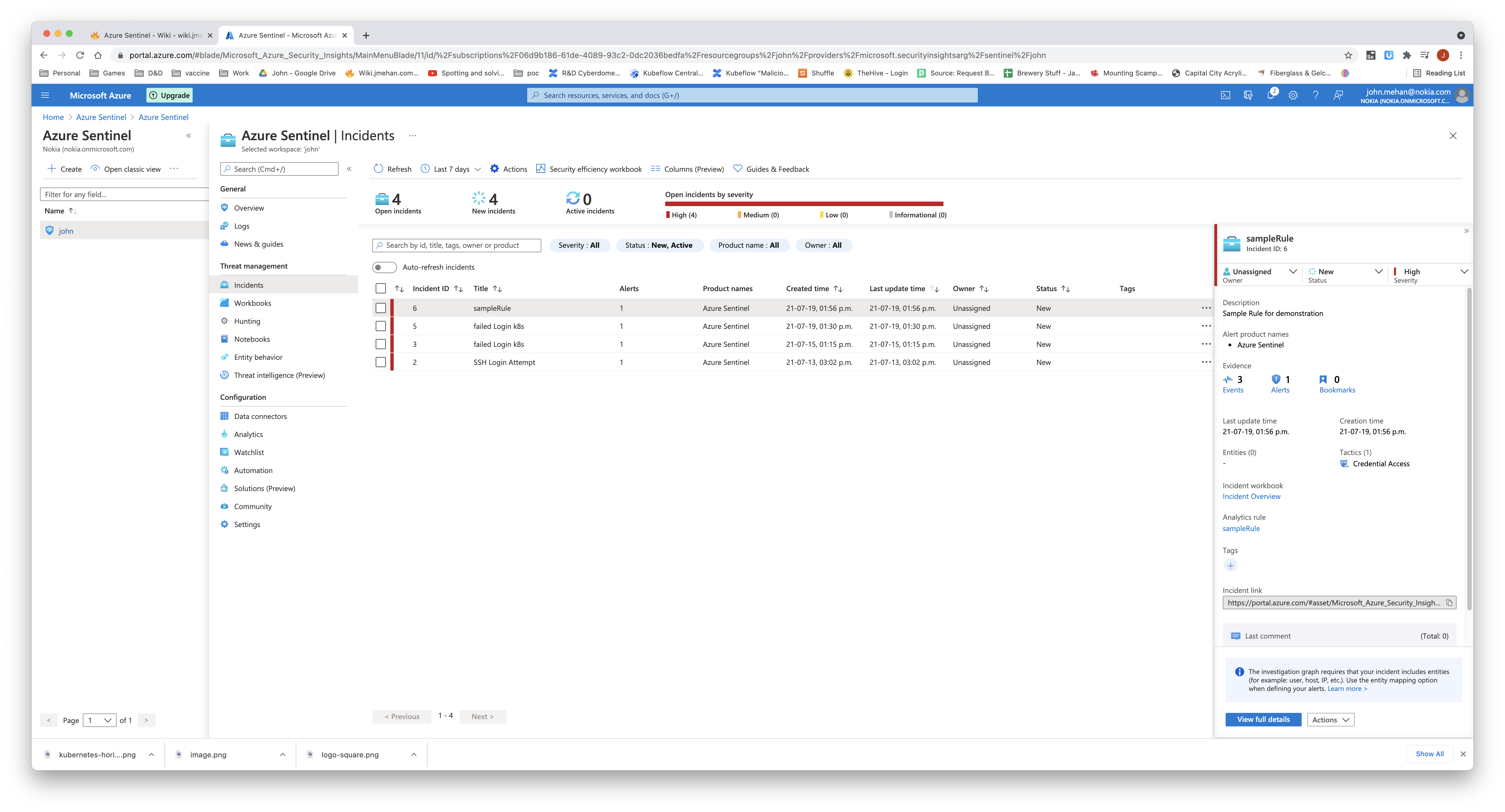
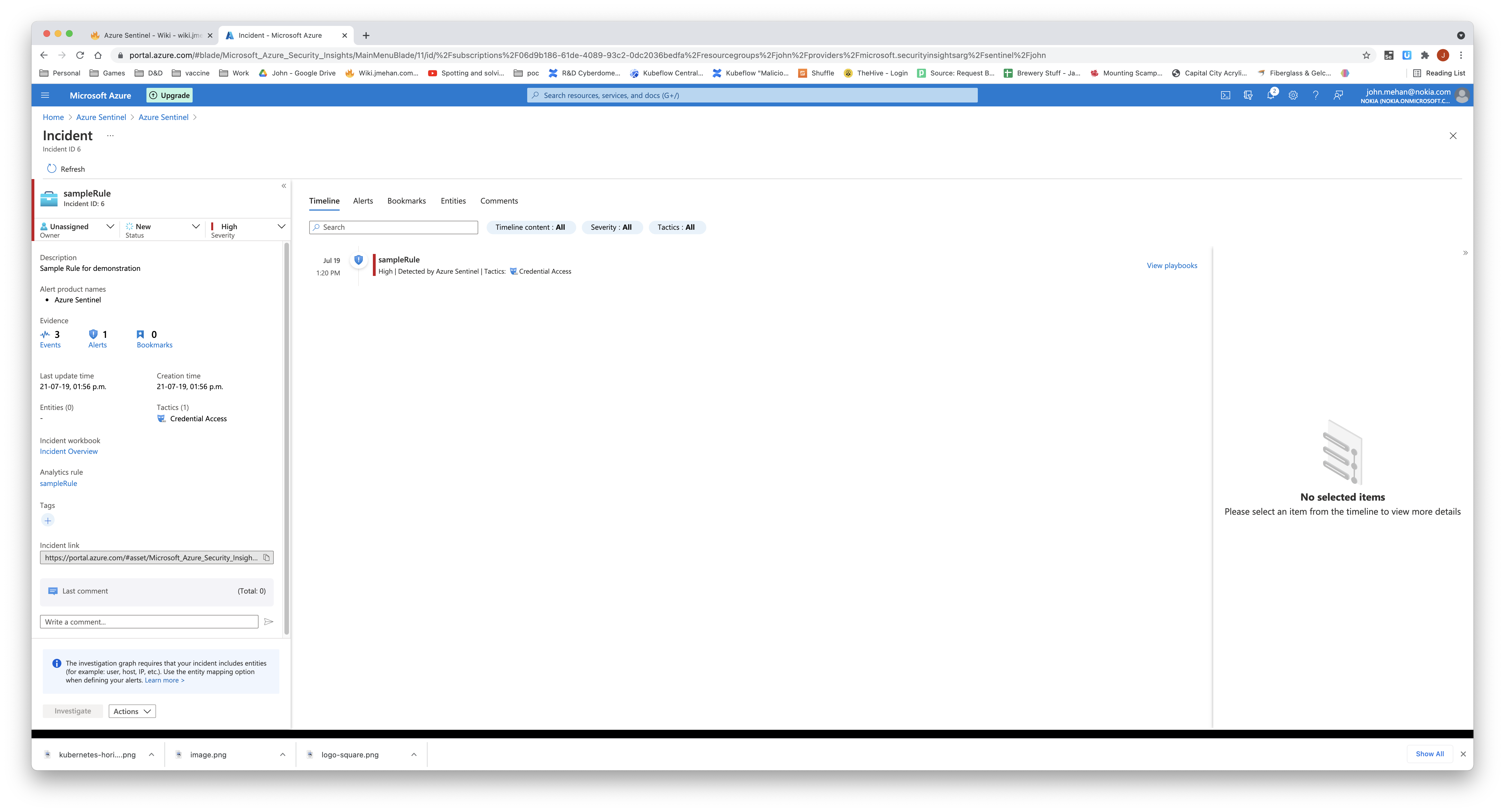
Incidents created from a analytics rule, can be displayed on the Incidents screen.
View details of the triggered incident by clicking the incident and clicking View Full Details.
Clicking Events will display the log records that triggered the incident.
References
| Reference | URL |
|---|---|
| What is Azure Sentinel and why you should care | Azure Tips and Tricks | https://www.youtube.com/watch?v=dRpOR2GpL1s |
| Azure Sentinel | https://azure.microsoft.com/en-ca/services/azure-sentinel/ |
| Azure Portal | https://portal.azure.com/#home |
| Samples for queries for Azure Data Explorer and Azure Monitor | https://docs.microsoft.com/en-us/azure/data-explorer/kusto/query/samples?pivots=azuredataexplorer |
| Tutorial: Create custom analytics rules to detect threats | https://docs.microsoft.com/en-us/azure/sentinel/tutorial-detect-threats-custom |
| Azure Sentinel Lab Series | Setup Syslog Collector and install Azure Sentinel Agent | EP1 | https://www.youtube.com/watch?v=KJbIH7egdVI |