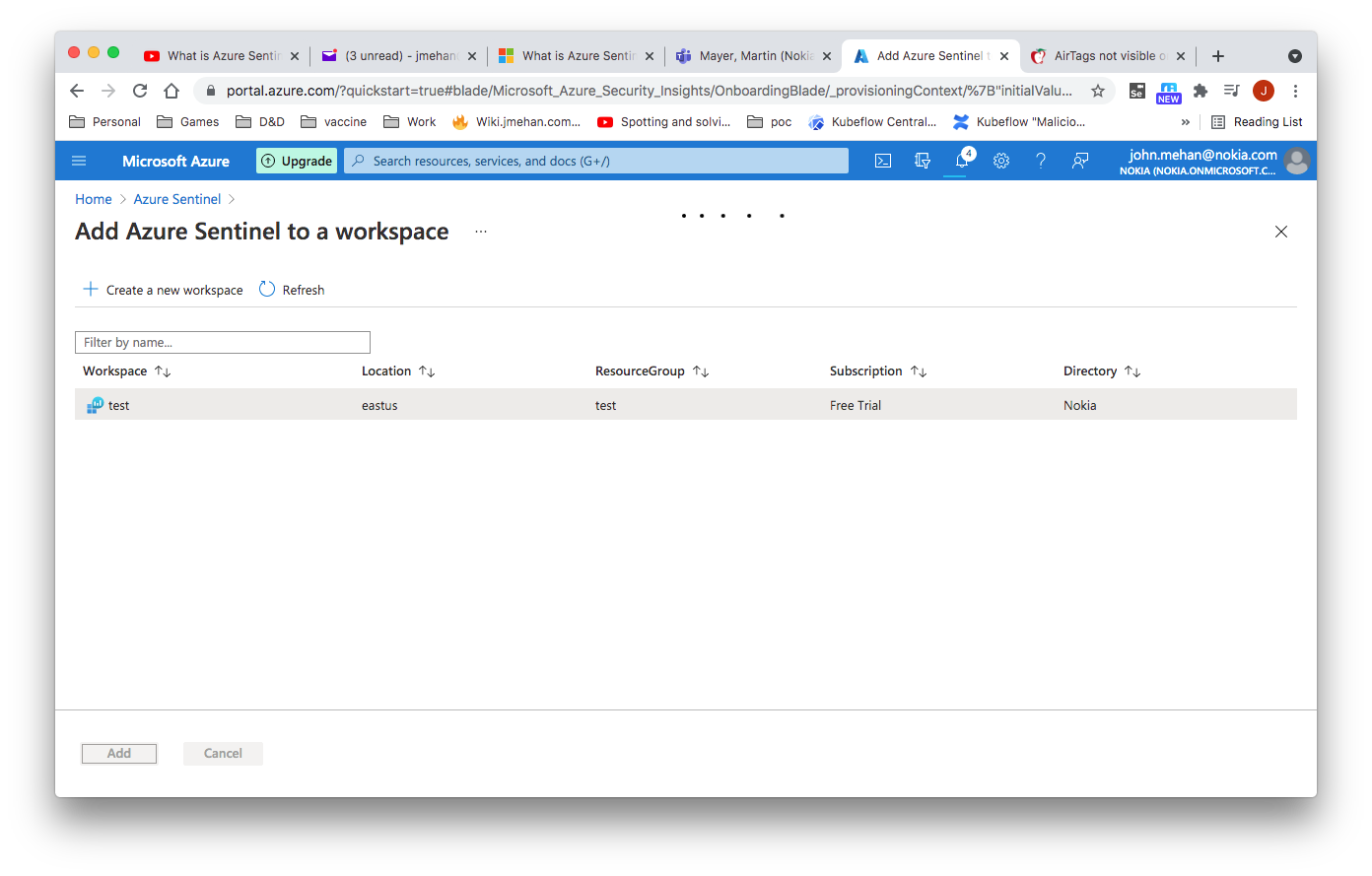
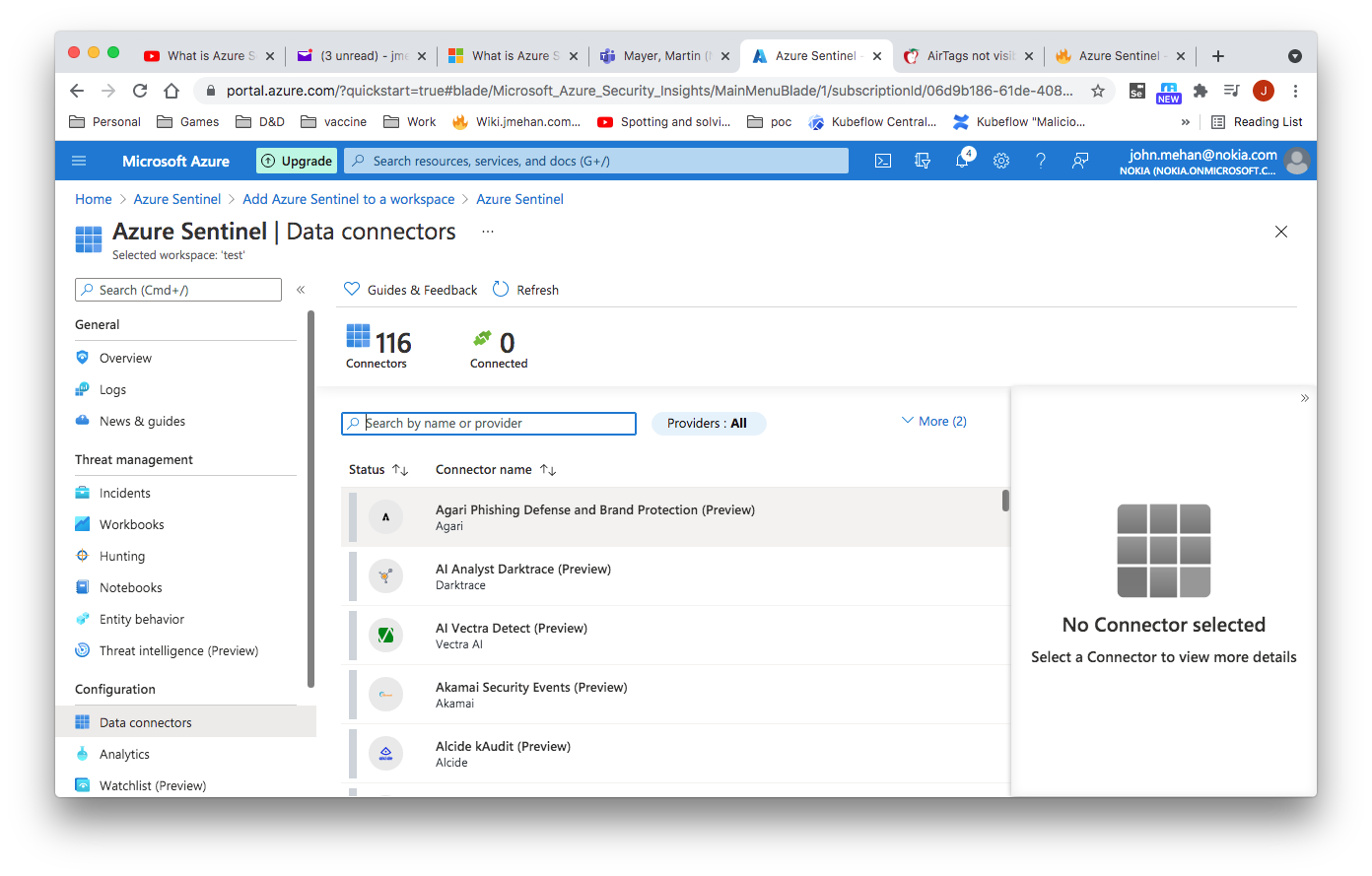
Create an Azure Sentinel Instance
https://azure.microsoft.com/en-ca/services/azure-sentinel/
https://portal.azure.com/#home
You will need to first search for Sentinel and then create a workspace. Then you can add a sentinel instance to your workspace.
Collect Data
Connectors
Kubernetes
Alcide kAudit (Preview)
Alcide kAudit connector automatically exports your Kubernetes cluster audit logs into Azure Sentinel in real time. The kAudit connector provides enhanced visibility and observability into your Kubernetes audit logs. Alcide kAudit gives you robust security and monitoring capabilities for forensics purposes.
For more information about connecting to Azure Sentinel, see Connect Alcide kAudit to Azure Sentinel.
Data ingestion method: Azure Functions and the REST API.
Supported by: Alcide
Syslog Connector
https://docs.microsoft.com/en-us/azure/sentinel/connect-syslog
Linux agent
wget https://raw.githubusercontent.com/Microsoft/OMS-Agent-for-Linux/master/installer/scripts/onboard_agent.sh && sh onboard_agent.sh -w xxx -s xxx -d opinsights.azure.com
Output
Uninstall
$ sudo /opt/microsoft/omsagent/bin/uninstall
Query Examples
Syslog
| where Facility in ("authpriv","auth")
| extend c = extract( "Accepted\\s(publickey|password|keyboard-interactive/pam)\\sfor ([^\\s]+)",1,SyslogMessage)
| where isnotempty(c)
| count
Syslog
| where Facility in ("authpriv","auth")
| where SyslogMessage contains "authentication failure "
| count
// Search in multiple tables
// Search both Syslog and Event tables for the term "login".
search in (Syslog, Event) "authentication failure"
| where TimeGenerated > ago(24h) // return records from the last 24 hours
// All Syslog with errors
// Last 100 Syslog with erros.
Syslog
| where SeverityLevel == "err" or SeverityLevel == "error"
| top 100 by TimeGenerated desc
//login errors
Syslog
| where SeverityLevel == "err" or SeverityLevel == "error"
| where Facility == "auth"
| where SyslogMessage contains "kex_exchange_identification"
//any auth errors
Syslog
| where SeverityLevel == "err" or SeverityLevel == "error"
| where Facility == "auth"
| count
//failed login
Syslog
| where Facility == "auth"
| where SyslogMessage contains "Failed password"
| order by EventTime asc
| count
//failed login with extraction of fields
Syslog
| where Facility == "auth"
| where SyslogMessage contains "Failed password"
| extend user = extract("Failed password for invalid user (.*) from (.*) port (.*) (.*)", 1, SyslogMessage, typeof(string))
| extend remoteIp = extract("Failed password for invalid user (.*) from (.*) port (.*) (.*)", 2, SyslogMessage, typeof(string))
| extend port = extract("Failed password for invalid user (.*) from (.*) port (.*) (.*)", 3, SyslogMessage, typeof(string))
| extend protocol = extract("Failed password for invalid user (.*) from (.*) port (.*) (.*)", 4, SyslogMessage, typeof(string))
| order by EventTime asc
References
| Reference | URL |
|---|---|
| What is Azure Sentinel and why you should care | Azure Tips and Tricks | https://www.youtube.com/watch?v=dRpOR2GpL1s |
| Azure Sentinel | https://azure.microsoft.com/en-ca/services/azure-sentinel/ |
| Azure Portal | https://portal.azure.com/#home |
| Samples for queries for Azure Data Explorer and Azure Monitor | https://docs.microsoft.com/en-us/azure/data-explorer/kusto/query/samples?pivots=azuredataexplorer |
| Tutorial: Create custom analytics rules to detect threats | https://docs.microsoft.com/en-us/azure/sentinel/tutorial-detect-threats-custom |